Assumptions in Your Falcon Deployment Can Leave You Exposed. Independent Validation Closes the Gaps.
This assessment gives you the operational assurance that your CrowdStrike EDR, XDR, SIEM, and SOC teams and/or Falcon Complete or third-party MDR are working as intended before a real attack puts them to the test.

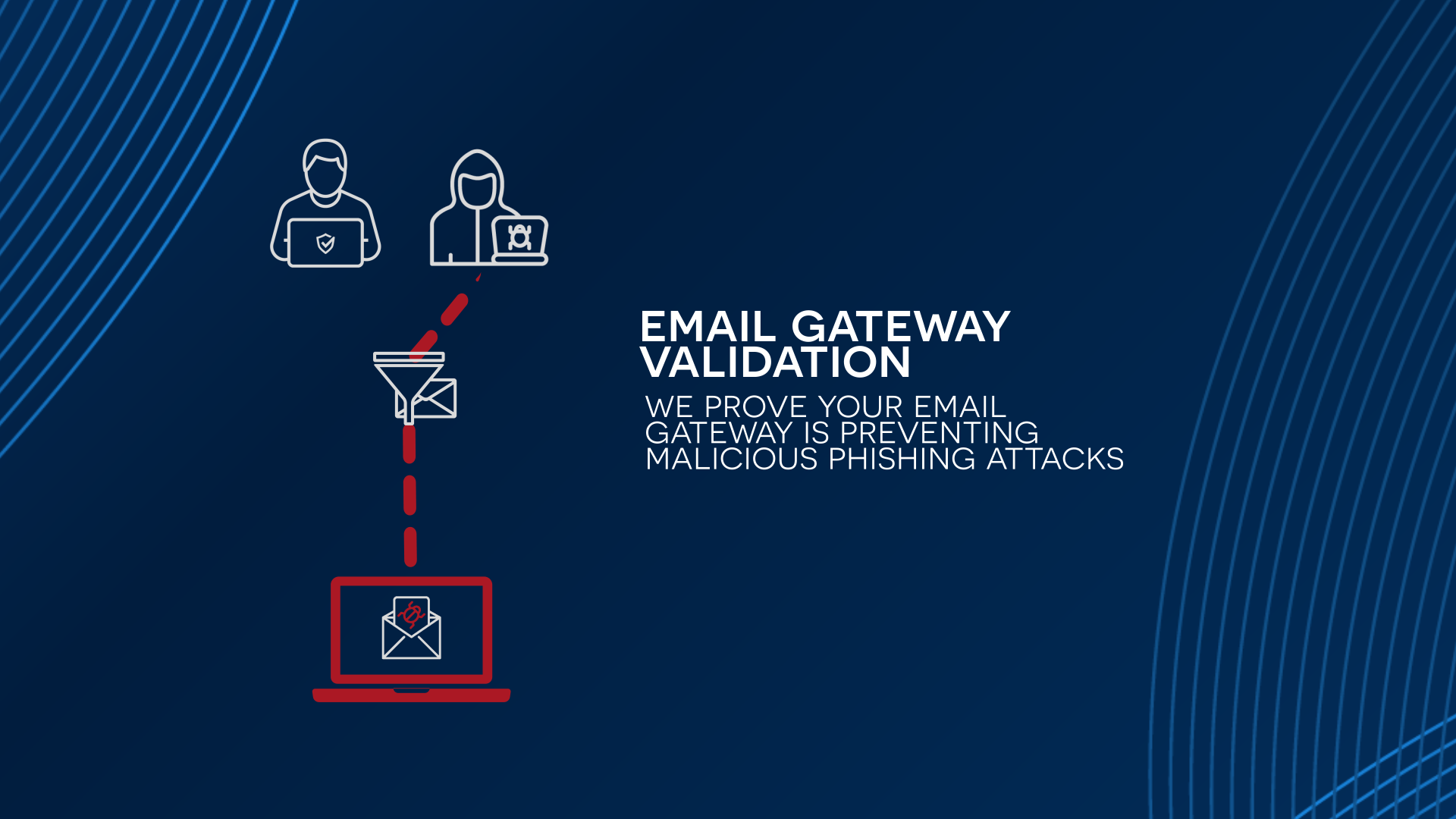
Validate Detection and Response Across Falcon
Simulated real-world actor TTPs test whether Falcon's EDR/XDR/SIEM trigger alerts and whether your SOC or Falcon Complete responds in time. Measure detection coverage, MTTD, and MTTR to ensure defenses perform when it matters most.
Expose Control Gaps Before They're Exploited
Simulated threats uncover inactive sensors, overly broad policies, misconfigured rules, and broken integrations—gaps that traditional audits and pentests miss. Identify real risks in your Falcon deployment before attackers do.
Give CISOs Confidence and the Board Proof
Validation results provide executive-ready reporting to show your CrowdStrike tools and teams are working as expected. Strengthen cyber governance, justify spend, and demonstrate due care to stakeholders and auditors.

Threat Detection Effectiveness
We emulate adversary behavior to validate whether Falcon’s EDR, XDR, and SIEM are properly configured, integrated, and actively detecting threats. We uncover misconfigurations, policy drift, default settings, and visibility gaps.

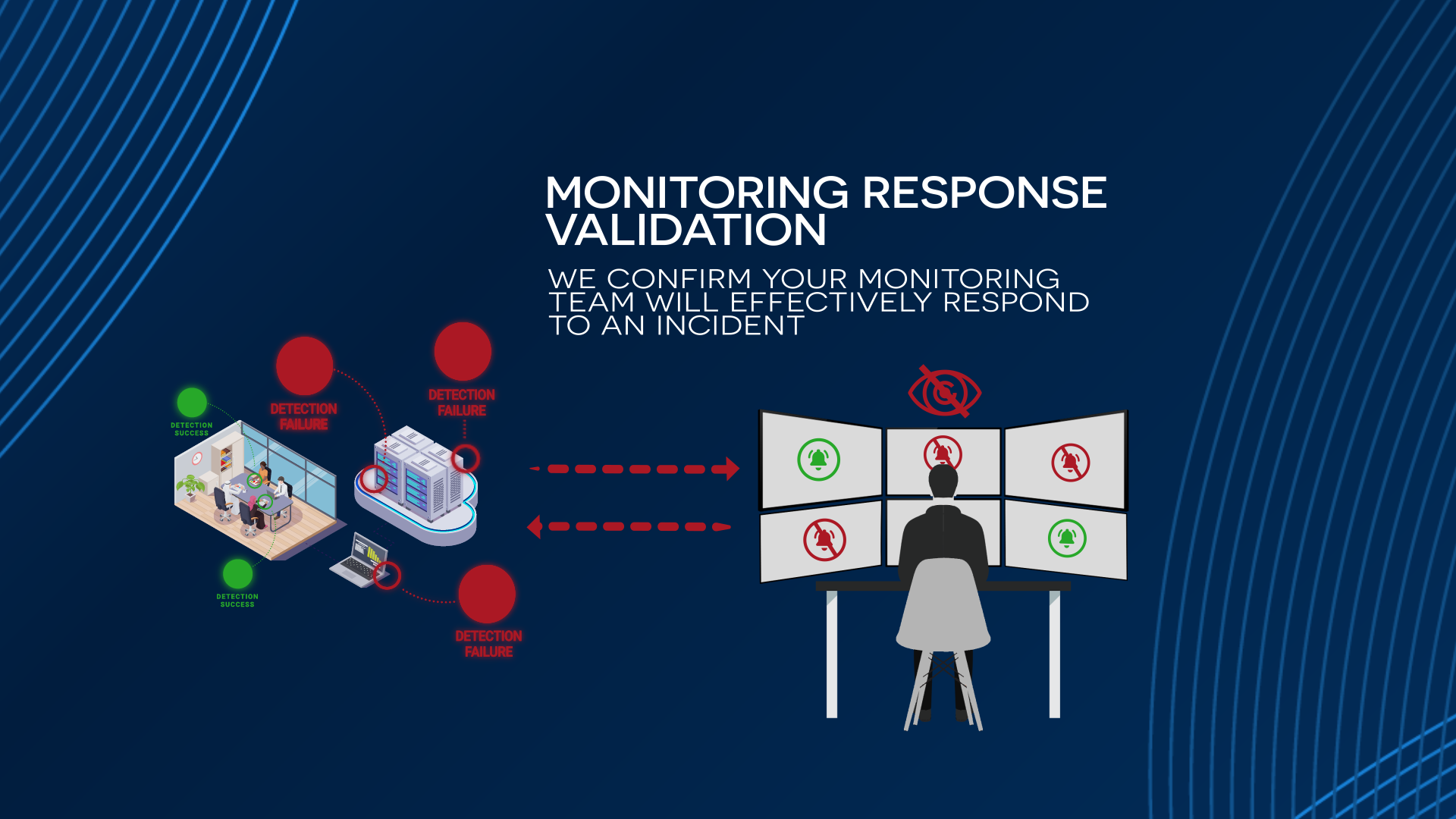
Threat Response Readiness
We test whether alerts generated by Falcon tools are seen, triaged, and acted on—either by your internal SOC team, Falcon Complete, or third-party MDR. We measure escalation performance against your response expectations or MDR SLAs.
Plan: We align on testing scope, target systems, and threat scenarios.
Emulate: Our team safely executes real-world attacks in your environment.
Validate: We confirm whether CrowdStrike tools and teams alert, block, and respond.
Report: You receive clear, actionable findings & recommendations with board-ready insights.
This isn’t a penetration test. It’s real-world attack emulation designed to validate the entire chain of defense across tools, teams, and tuning.
No Breach & Attack Simulation (BAS) platform to license or manage
No red or purple team resources required
Fully managed by OnDefend using our proprietary BlindSPOT™ platform
Can bundle into your annual penetration test budget
Even with the best tools and vendors, real-world assurance only comes from independent security control validation.
We validate your CrowdStrike controls and team performance so you know your security operations are actually working as intended.
.png?width=1200&name=Threat%20Detection%20Assessments%20(1).png)
Let’s walk through how security control validation works—and how to ensure your Falcon platform is tuned, tested, and ready for real-world threats.