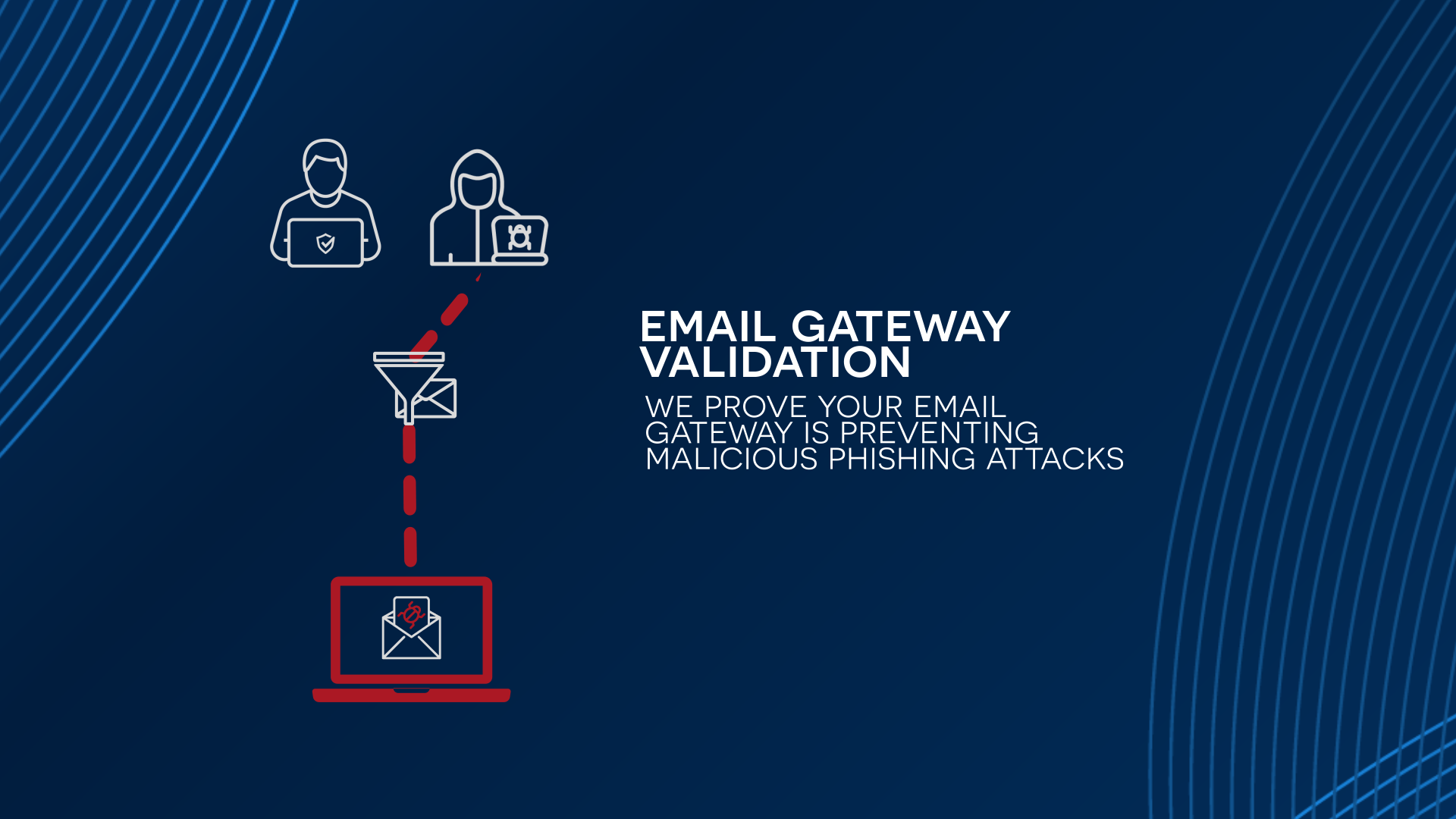

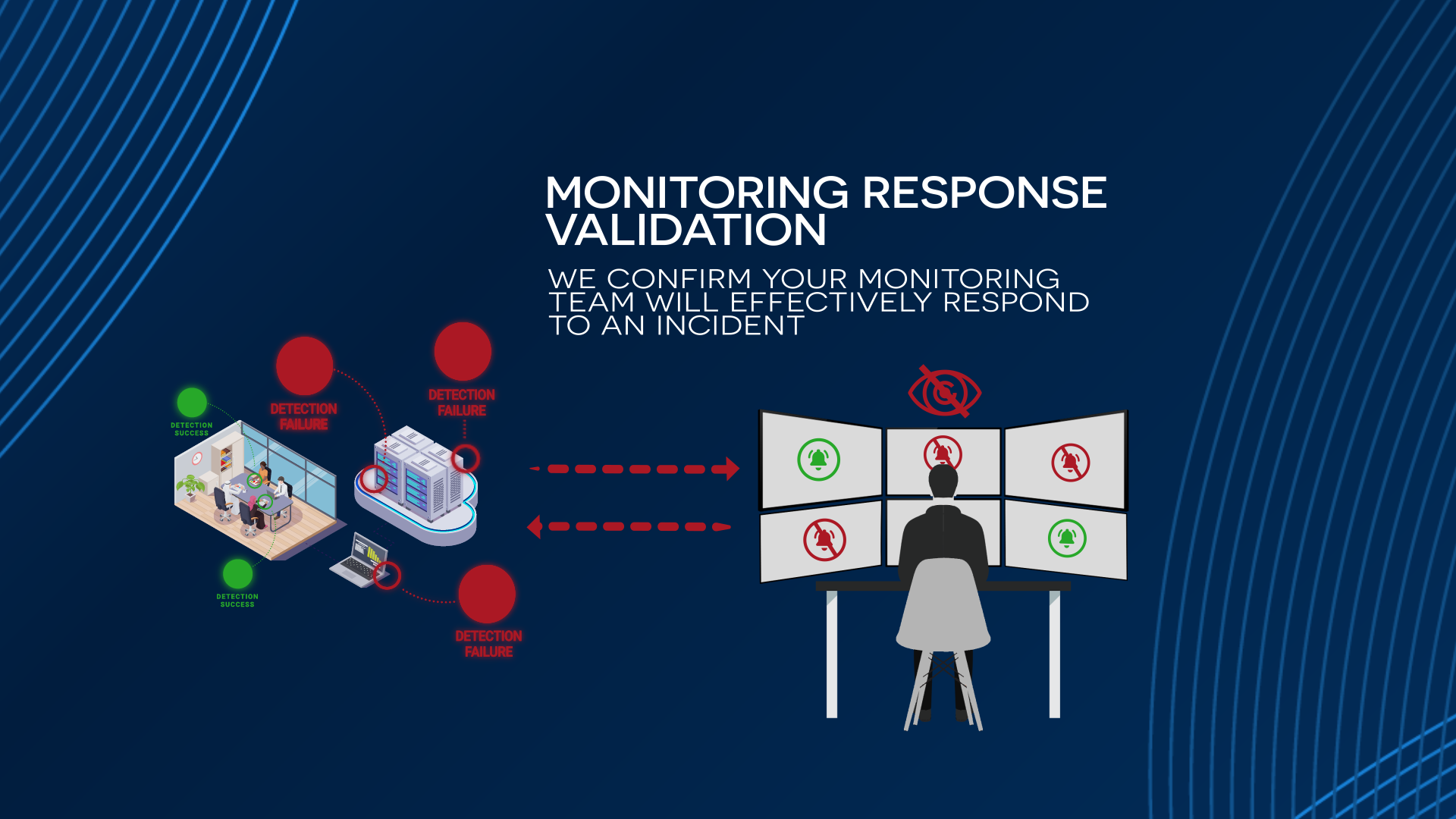
Security Control Validation simulates real-world cyber-attacks to consistently ensure your secure email gateway is effectively filtering malicious emails, threat detection tools are detecting real-world attacks, and threat response teams are neutralizing threats in real-time.

Explainer video introducing email gateway validation, threat detection validation, and threat response validation. (Also referred to as "Ransomware Defense Validation")
Watch Video
Revealing and Removing the Hidden Risks of Security Control Failures (Also referred to as "Security Control Validation")
Watch

A comprehensive guide explaining how security control validation simulates real-world cyber-attacks to consistently ensure the secure email gateway effectively filters malicious emails, threat detection tools detect real-world attacks, and threat response teams neutralize real-time threats.
Download PDF
Learn how a leading U.S.-based healthcare system enhanced its ransomware resilience by validating security controls, ensuring vendor accountability, and strengthening defenses to protect critical patient data and care continuity.
Download PDF
This healthcare system is moving past compliance checkboxes to reimagine security control validation. Discover how they’re validating defenses, identifying coverage gaps, and demonstrating ROI on security investments with OnDefend’s Security Control Validation program.
Download PDF
Explore why security controls like SEGs, EDRs, and MDRs fail and learn proactive strategies to optimize threat detection, response, and resilience with OnDefend.
Read Blog

Traditional security assessments and out-of-the-box tool configurations aren’t enough to protect against adversaries.
Read Blog
Misconfigurations and alert gaps can silently weaken your CrowdStrike deployment. Here’s how to validate controls and gain operational assurance.
Read Blog
Most security teams talk about MITRE ATT&CK coverage. But attackers don’t care about your roadmap. Here’s how OnDefend combines penetration testing, attack simulations, and tabletop exercises to proactively validate security controls and prepare teams for real-world threats.
Read Blog
Most companies run external penetration tests to meet compliance requirements, but those only tell part of the story. We explain the difference between external and internal penetration testing, why both matter, and what we see in real-world environments.
Read Blog
Penetration testing identifies vulnerabilities, but it doesn’t confirm whether your detection tools and response teams will stop real threats. Learn how combining pentesting with continuous threat detection and response validation strengthens your cybersecurity posture.
Read Blog